With Microsoft Endpoint Manager (Intune) we have the possibility to limit the sensitive data which is shown in Outlook mobile notifications. This might be a (security) requirement in your company as such email and calendar notifications might contain sensitive data. These notifications are visible from the lock screen, everybody who gets his hands on the phone is able to read these notifications without unlocking the device.
To accomplish this limitation for mobile notifications we use an Intune App Protection policy to set the notification to Block org data. This blocks the sensitive data in the notification, but still shows a notification to inform the user an email is received or a meeting is about to start.
If you`d like to only block the sensitive data in email notifications and to allow calendar notifications to show some more information an App Configuration policy needs to be created besides the App Protection policy.
In this article we have a look how the App Protection and Configuration policies are created and what the minimum settings are to block organization data in email notifications and allow the calendar notifications.
Off-course we also have a look at the end-user experience, as this feature might have a pretty big user impact.
Create an App Protection policy
As described, we need to create an App Protection Policy in Intune to block org data in the (Outlook) mobile notifications. In the example I set the notification to block org data, the other option is to block all notifications. That option even has a bigger impact, as all notifications are blocked.
- Sign-in to the Endpoint Manager admin center
- Browse to Apps – App protection policies
- Click +Create policy
- Choose iOS/ iPadOS or Android
- Give the profile a Name
- Enter a Description (Optional)
- Click Next
- Leave Target to apps on all device types switched to Yes
- Click Select public apps
- Search for Outlook
- Select Outlook – Click OK
- Click Next
- Select Block org Data for Org data notifications
- Make your choice on all other data loss prevention controls
- Click Next
- Make your choice on all PIN and credential requirements
- Click Next
- Make your choice on all sign-in security requirements
- Click Next
Finish the wizard by assigning the policy to a security group.
Create an App Configuration policy (optional)
The creation of an App configuration policy is optional. You only create this policy if you want the calendar notification to show org data instead of blocking this. You actually create an exclusion with this policy on the App protection policy created in the previous step.
- Browse to Apps – App configuration policies
- Click +Create policy
- Select Managed apps
- Give the profile a Name
- Enter a Description (Optional)
- Click Select public apps
- Search for Outlook
- Select Outlook (both versions) – Click OK
- Click Next
- Select Allowed for Calendar notifications
- Click Next
Finish the wizard by assigning the policy to a security group.
End-user experience
Let`s have a look at the end-user experience.
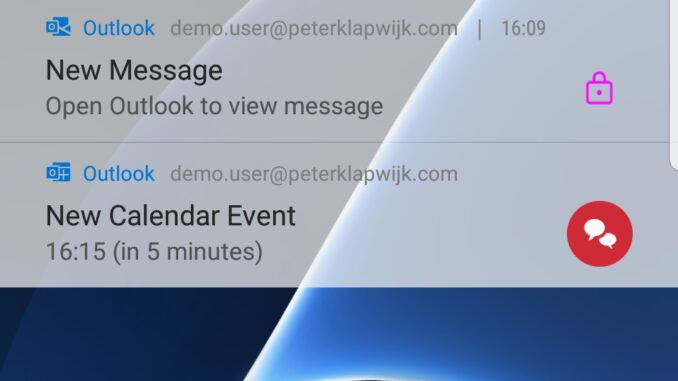
When we have only created and deployed the App protection policy, for both notifications the org data is blocked.
If we also created and deployed the App configuration policy, org data is blocked for email notifications. The calendar notification shows org data, as Team meeting is the subject of this calendar item.
To conclude, this setting has a huge impact on the user experience. Where I thought org data would be shown as soon as the device is unlocked, it`s not. When I unlock the device, org data is still blocked. I need to open Outlook to see who send me an email, which I found pretty annoying.

is there any way to show the org data once the device is unlocked?
thanks!