Wiping a mobile device, with Android or iOS as OS, after a number of sign-in failures is a commonly used Intune setting to protect the device and corporate data against unauthorized acces. Since the release of the MDM Security Baseline in Microsoft Endpoint Manager (Intune) a comparable setting is available for Windows 10 devices.
The setting is found in the Device Lock section of the Security Baseline and called Number of sign-in failures before wiping device. The description of the setting states The number of authentication failures allowed before the device will be wiped. A value of 0 disables device wipe functionality.
This is actually not completely true as the behavior is that the device is rebooted after a number of authentication failures and not wiped, but locked in the BitLocker recovery wizard. If the user is able to retrieve the recovery key, the user can gain access again to the device.
As the Windows device is locked in BitLocker recovery mode, a prerequisite of this setup is the device is encrypted with BitLocker. If the device is not encrypted with BitLocker, the device is not wiped and not locked, it reboots and the user can try to sign-in again.
Configure MDM Security Baseline
The setup is pretty simple, as it is just creating the MDM Security Baseline and assign it to your devices. But keep in mind by creating a Security Baseline, by default all settings in the baseline are enabled.
- Sign-in to the Microsoft Endpoint Manager portal
- Browse to Endpoint security – Security baselines
- Click MDM Security Baseline under Windows 10 Security Baselines
- Click Create profile
- Give the profile a Name
- Enter a Description (optional)
- As this is the only Baseline version, that option is greyed out
- Click Next
- Scroll down to the Device Lock section
- Change the value of Number of sign-in failures before wiping device to your needs or leave it at the default value of 10
- Review all the other settings in the Baseline
- Change the settings to your needs
- Click Next
- Select a scope if you use scoping on the Scope tags tab
- Click Next
- Select a security group to assign to policy to or choose a group from the drop-down list
- Click Next
- Verify your settings
- Click Create
End-user experience
Let`s move over to a Windows 10 device on which the policy is applied. Enter a few times a PIN or password which is wrong.
After a few times of authentication failures the Windows logon screen is locked with a warning message:
The password isn`t correct. Be careful – if you keep entering the wrong password, you`ll be locked out to help protect your data.
To unlock, you`ll need a BitLocker key.
Press Ctrl+Alt+Delete to unlock.
When the user unlocks the screen, another message is shown with a challenge phrase.
The user needs to enter A1B2C3 before he can move further.
After the challenge phrase is entered successful, the user is allowed to try to authenticate another time.
If the authentication fails again, the device is locked and the user needs to restart the device.
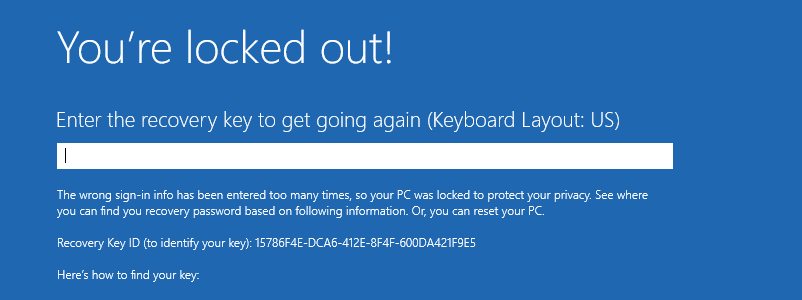
When the last authentication also fails, the device is restarted and locked in the BitLocker recovery screen.
Depending on the BitLocker setup, the user can lookup the BitLocker recovery key himself via myprofile.microsoft.com or needs to contact the servicedesk.
Happy testing!

Well Done, thanks Peter!
Is there any way to set this without a Security Baseline, I don’t like the excessive options that are set.
Can’t find it in Settings Catalog, maybe a custom OMA policy?