This is the fourth blog post about managing local users and local rights on Windows 10 devices with Microsoft Intune. In this blog post I show how we can manage the local administrators group on a Azure Azure AD joined Windows 10 device.
The configuration is almost equal to how we manage the local administrators group on a Hybrid Azure AD (AAD) joined Windows 10 device. The difference is found in the already present members of the local Administrators group, on AAD joined devices, the Global Administrator and Device Administrator (roles) are the default members of the local Administrator group.
So these roles could also be used to provide local administrator rights on the AAD joined devices. But the rights of the Global admin role could be a little too much for this. And these rights are provided to all AAD joined devices, where it might be required to limit the number of devices where an (admin) user is administrator. You might want to provide to local IT of a country administrator rights only to the devices of that country.
Like in the previous posts we need to use a Configuration Service Provider (CSP) policy and a Custom configuration profile to get the job done. And as with managing the Hybrid AAD joined devices, we need to use the RestrictedGroups CSP.
All information for this CSP policy is found on Microsoft docs here.
Some notes to take into account; this policy overwrites the default members of the Administrators group. By default the Global Administrator and Device Administrator (roles) are member of the local Administrators group. If you only want to add a group to the Administrators group and not want to remove the default groups, don`t forget to add the Global Administrator and Device Administrator to your policy. And add the local Administrator account to the policy, otherwise it fails.
As these roles are added to the local Administrator group by SID, take note of these before you overwrite these.
Configure the Custom Configuration profile
- Sign-in to the Endpoint Manager admin center
- Browse to Devices – Windows
- On the Configurations profiles tab click + Create profile
- Choose Windows 10 and later as Platform
- Choose Custom as Profile type
- Click Create
- Give the configuration profile a Name
- Enter a Description (optional)
- Click the Settings tab
- Click Add
In the value field we set which group membership we like to manage and define the group members.
<accessgroup desc> contains the local group SID or group name.
<member name> contains the group members to add to the local group.
In the example, I add the default members of the group to the policy; the local Administrator account, the Global Administrator and Device Administrator (with the SID). And I add one extra AAD user account in the form of AzureAD\UPN.
Enter below information to the Row;
Name: RestrictedGroups – ConfigureGroupMembership
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/RestrictedGroups/ConfigureGroupMembership
Data Type:
<groupmembership>
<accessgroup desc = "Administrators">
<member name = "Administrator" />
<member name = "S-1-12-1-2934938113-1096209395-2588194479-178906382" />
<member name = "S-1-12-1-766653809-1274192161-2093628596-1982031183" />
<member name = "AzureAD\demo.user@peterklapwijk.com" />
</accessgroup>
</groupmembership>Click OK (twice) and click Create.
Assign the profile to a security group and your ready for testing.
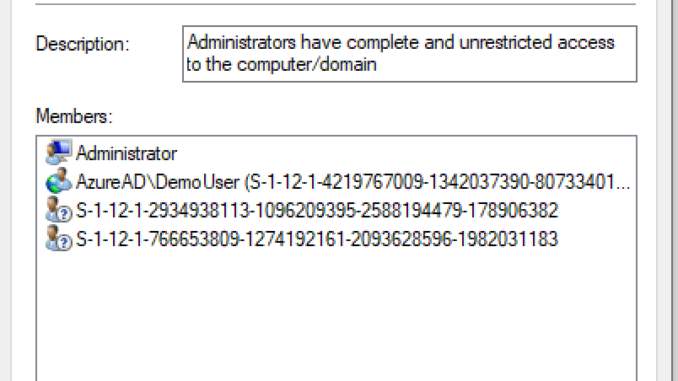
The end result
The end result is the default members are still member of the local Administrators group. The extra Azure AD account is added to the local Administrators group.
That`s is for this post. Thank you for reading!
If you`d like to know how an Azure AD group can be added to the local administrators group, read this follow-up post.
Starting with Windows 10 build 20H2 we also have a new setting LocalUsersAndGroups.

thank You for the file, i would like to ask you something about this:
where it says “Assign the profile to a security group and you’re ready for testing.“, do I add “Device” security group or user group to that profile?
I would recommend a device group.
How do I write the value for value box to indent lines like “member name” as shown in the screenshot?
No need for that, that happens when you paste in the text.
I first write the value in a notepad file and paste it in the value box.
I tried this, and i am getting a ‘Remediation failed’ error when i assign to my Windows 10 device. End result is that user still does not have admin rights. I am running version 1903… what version is this compatible with? I see that the follow-up article (group assignment) is only version 2004..
This setting is added in 1803, reference https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-restrictedgroups
The follow-up article is about using groups, indeed supported since 2004.
Make sure the OMA-URI and value are correct. Don`t just copy/ paste from the article as WordPress replaces the correct double quotes with different quotes, which causes issues.
Thank you Peter- this worked just fine 😀
I did post in Manage the local administrators group with Microsoft Intune – Hybrid AAD joined Windows 10 devices.This CSP Policy is OS language dependent.
It works fine with english operative system.
I´ve been 3 days working on it and it did only worked when I used the spanish name of administrators group and local administrator user
Administradores and Administrador.
404 event id
Hola Francisco, creo que hablas español, queria hacerte una consulta. Cuando aplicaste la politica agregaste el nombre del grupo de administradores local en español o en ingles??? administradores o Administrators???? accessgroup y groupmembership si es en inlges, cierto?
Si esta en ingles
hi. How do I use it to add an Azre Ad group. With SID or groupname? And how to specify it?
Have a look at the follow-up article on that topic https://www.inthecloud247.com/add-an-azure-ad-group-to-the-local-administrators-group-with-microsoft-intune/
Hello all.
I would not advise to just allow local users to login to the kiosk device. Make sure you also add for example global admins and devices admins. This way you can login with an account for troubleshooting. When login in with a Global Admin account, the kiosk policy is not active and you can do all kind of management and troubleshooting tasks. For example see the AppLocker eventlog to see which apps are being blocked.
You can add the global admin and device admin with their id. I did this by checking the local administrators group on the device to get the id’s.
Another comment is to use a Self Deploying autopilot profile. With this the connection is set at a device level to Intune so sync with Intune is not reliable on the user which you will have with a user drive autopilot profile. Be aware that tasks like Powershell scripts which are set to run in the users content will never run for the local kiosk user so make sure everything is set to the device level.
Talking about Powershell, I did some actions based on a Powershell scripts which creates a scheduled task to make it run at the defined triggers moments. To make this work, make sure you add Powershell.exe 64bit and/or 32bit to be allowed with Kiosk. Else does Powershell tasks will never run because they will be blocked.
Hopefully this helps.