Today’s blog post is about sending a report to end-users with a report of the security recommendations from the Microsoft 365 Defender security portal.
The thought behind sending such a report to the end-user is that a company has users with local administrator permissions (developers for example) on their (Windows) device and these users install applications that are not maintained by the IT organization. The applications which are deployed by the IT organization are most likely updated by the IT organization on a regular basis. But the applications which are installed by the user themselves, are most likely not (updated by the IT organization). To make these users aware of the outdated applications on their devices, I wanted to send them a report once in a while.
In the Microsoft 35 Defender portal, we have information available on software that needs an update under the Security recommendations section of every device. If we can grab that information and filter out the software updates (or you might want to send a report with all the recommendations, you don’t filter anything out), we can create a simple report and send that to the owner of the device.
Let’s have a look at how we can send this report and what the requirements are.
The solution can be easily deployed with Bicep files, which can be found on my GitHub repo.
The solution in short
We can retrieve the devices with their recommendations via the WindowsDefenderATP API. We can query this information using HTTP actions in a Logic Apps flow. We need to retrieve the registered owner of a device (so we know the e-mail address to which we need to send the report), which is possible using Microsoft Graph and also with an HTTP action. The report we can create in this flow is sent via e-mail.
Requirements
For this solution, we have some requirements. To retrieve information from the Microsoft Defender and Azure AD via APIs we need to have permission to perform the job. There are different options to authenticate to the security center API and MS Graph and assign permissions, but I prefer an Azure Managed Identity.
The required Microsoft Graph (Application) permissions we need are:
Device.Read.All
User.Read.All
The required WindowsDefenderATP permissions are:
SecurityRecommendation.Read.All
Machine.Read.All
To send the report via email, we need to have a (shared) mailbox. I used a service account with permission to send an email from a shared mailbox.
Setup the Logic Apps flow
When the requirements are met, we can start building our Logic Apps flow.
Sign in to the Azure portal and open the Logic App service. I created a blank Logic App of type Consumption.
When the flow is created, click on the name of the flow at the top of the screen, open the Identity section, and on the tab User assigned add your Managed Identity.
Open the Overview tab, which shows a few templates, and choose Recurrence.
Change the interval settings to your needs.
The first action we add is an HTTP Action, to query for the machines via the security center API.
I don’t query all devices available in Defender, I only query the machines of the developers which have a tag assigned (in my example DevComputers). As you can see this is done using the findbytag API.
As the query by default returns a lot of information that I don’t use, I use a $Select to only select the values I’m interested in.
Add an HTTP Action.
Select GET as Method.
Enter below URI:
https://api.securitycenter.microsoft.com/api/machines/findbytag?tag=DevComputer&$select=id,computerDnsName,osPlatform,healthStatus,aadDeviceIdChoose Add Parameter and select Authentication.
As Authentication type select Managed identity.
Select your Managed identity from the list.
And add https://graph.microsoft.com as Audience.
Next, we need to add a Parse JSON action (which is a Data operations action). We parse the output of the HTTP action, to be able to use the values later on in the flow.
As Content, we select Body from the Dynamic content list that is a value from our HTTP action.
As Schema, we can run the current flow (without the Parse JSON action), open the run via runs history, and grab the body from the HTTP action. Then add it via the Use sample payload option to create the schema.
This is the schema that you use when you use the exact same URI in the HTTP action:
{
"properties": {
"@@odata.context": {
"type": "string"
},
"value": {
"items": {
"properties": {
"aadDeviceId": {
"type": "string"
},
"computerDnsName": {
"type": "string"
},
"healthStatus": {
"type": "string"
},
"id": {
"type": "string"
},
"osPlatform": {
"type": "string"
}
},
"required": [
"id",
"computerDnsName",
"osPlatform",
"healthStatus",
"aadDeviceId"
],
"type": "object"
},
"type": "array"
}
},
"type": "object"
}I only want to send a report to the owner of a device that has an active status in Microsoft Defender. Therefore I use a filter array action, which is also a Data operations action.
When the health status is equal to active, the data is present as output of the filter array action and inactive machines are filtered out.
Add the Filter Array action.
In the left box add healthstatus which is found in the Dynamic content list as a value of the Parse JSON Action. Select is equal to from the drop-down list and enter Active in the right box.
Now that we have information on our active dev machines, we need to query the API for the recommendations per machine with another HTTP action. As you can see I use $filter to only retrieve recommendations of type Update (remove everything recommendations to query all recommendations).
Add an HTTP Action.
Select GET as Method.
Enter below URI:
https://api.securitycenter.microsoft.com/api/machines/[ID]/recommendations?$filter=(remediationType%20eq%20'Update')Replace [ID] with the ID retrieved from the filter array action. This will add the HTTP Action in a For each action.
Add the authentication information.
This time we don’t parse the output from the HTTP action but use a Select (Data operations) action.
In the From field, we add this expression which retrieves the value data from the HTTP actions body:
body(‘HTTP_GET_recommendations’)?[‘value’]
Next enter the information in the Map fields like below.
Here we map the information from the HTTP action to a value name, which we use later in the flow.
To map the values, we use an expression on every row:
item()?[‘relatedComponent’]
item()?[‘recommendationName’]
item()?[‘vendor’]
item()?[‘recommendedVersion’]
This is our Select action.
We also query machines that don’t have a recommendation. These machines will return an empty value in the output of the Select recommendation action, on which we can filter out these devices.
Add a Condition (Control) action.
In the left box add this expression:
empty(outputs(‘Select_recommendations’)?[‘body’])
Select is equal to from the drop-down list and enter false to the right box.
To retrieve the registered owner of a device, we first query via Microsoft Graph for the Azure AD device object as we have the aadDeviceId retrieved and no usable information on the user.
Add an HTTP Action.
Select GET as Method.
Enter below URI:
https://graph.microsoft.com/v1.0/devices?$filter=(deviceId%20eq%20'[aadDeviceId]')&$select=id,deviceId,displayNameReplace [aadDeviceId] which you find as Dynamix content from the filter array action.
Add the authentication information.
Parse the output from the HTTP action.
This is the schema:
{
"properties": {
"@@odata.context": {
"type": "string"
},
"value": {
"items": {
"properties": {
"deviceId": {
"type": "string"
},
"displayName": {
"type": "string"
},
"id": {
"type": "string"
}
},
"required": [
"id",
"deviceId",
"displayName"
],
"type": "object"
},
"type": "array"
}
},
"type": "object"
}With this HTTP action, we retrieve the registered owner of the devices.
Add an HTTP Action.
Select GET as Method.
Enter below URI:
https://graph.microsoft.com/v1.0/devices/[ID]/registeredOwners?$select=id,displayName,userPrincipalName,mailReplace [ID] with the ID from the last Parse JSON action. This will add the HTTP action in a For each action.
Add the authentication information.
And we use another Parse JSON action, with the below schema:
{
"properties": {
"@@odata.context": {
"type": "string"
},
"value": {
"items": {
"properties": {
"@@odata.type": {
"type": "string"
},
"displayName": {
"type": "string"
},
"id": {
"type": "string"
},
"mail": {
"type": "string"
},
"userPrincipalName": {
"type": "string"
}
},
"required": [
"@@odata.type",
"id",
"displayName",
"userPrincipalName",
"mail"
],
"type": "object"
},
"type": "array"
}
},
"type": "object"
}With a Create CSV table (Data operations) action we can create a simple CSV table with an overview of the retrieved recommendations.
Add Output, from Select recommendations action in the From field and select Automatic at the Columns drop-down.
And as last we add an action to send an email with the CSV report.
you can enter your own information in the Body and subject field. I added displayName from the registered owner and the device to the fields. And I used the mail from the registeredowners action.
Select Add parameter, to add an attachment.
As Attachments content add the Output from the Create CSV table action. And enter an attachment name.
And there he is, our Logic Apps flow:
End result
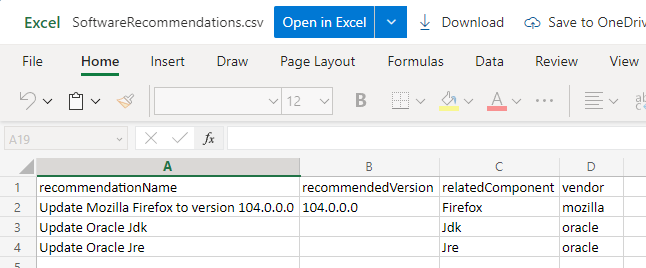
And this is our end result.
The end user receives an e-mail with a CSV sheet with an overview of the security recommendations.
In my case, this is an overview of applications that need an update.
That’s it for this blog post.
Thanks for reading!

Nice! Any idea on how to best do this from a MSP tenant > customer tenants, with the partner API?