I recently got some questions about Azure AD Conditional Access policies and multi-factor authentication (MFA) from a follower of this blog. The requirement was to secure Office 365 with MFA. But when an user was using an Intune managed device which was compliant, MFA was not necessary.
A Conditional Access (CA) policy was active and users where challenged with MFA prompts, but even when using a compliant device.
The ‘issue’ at this particular case was that MFA wasn`t enabled via a CA policy, but via the Office Admin portal. With this setup MFA is always required, as the MFA requirement is not part of the CA policy. The compliance status cannot be used as exemption of the requirement for MFA.
In this post I explain how Azure Active Directory Conditional Access policies can be used to keep your data safe, but also to keep a good user experience.
Before we begin, what is a Conditional Access policy in short?
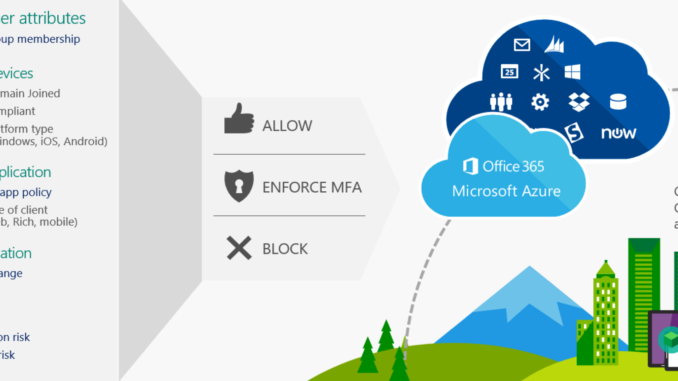
Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies. Actually it`s the principle of, if this, than that.
If your device is compliant, than you are granted access to Office 365. If your device is not compliant, access is blocked.
Azure AD Conditional Access is an Azure AD Premium feature.
Example setup
In this example I want my users to be challenged with Multi-Factor Authentication when they access SharePoint Online. But when an user is using a compliant device, they shouldn`t receive a MFA challenge.
To be sure the MFA requirement isn`t by-passed, I also want to block legacy authentication.
As complementary setting on the unmanaged (not compliant) device, I want to restrict downloading, printing and syncing documents from SharePoint or OneDrive.
Configure a Conditional Access policy for SharePoint
The Conditional Access section can be found in the Azure and Endpoint Manager (Intune) portal.
- Sign-in to the Azure portal
- Browse to Azure Active Directory – Security
- Choose Conditional Access
- Or sign-in to the Endpoint Manager admin center
- Browse to Endpoint Security
- Choose Conditional Access
On the Policies tab all existing Conditional Access policies are shown and here you create a new policy.
- Click +New policy
The policy consists of two parts; Assignments and Access controls.
Under Assignments you set to which, what, where the policy set is applied.
Think of which group of users, what kind of devices (Operating system), which location and which cloud app.
Under Access controls you determine if access is blocked, or granted under certain controls. And here you find the session controls.
Let`s create a CA policy and see what options are available for configuration.
- Give the Policy a Name
- Click Users and groups
On the Include tab we determine to who the policy is applied. The policy can be assigned to All users, but you can also assign it to All guest and external users, Directory roles or Users and Groups (or a combination of these options).
If we choose Directory roles, we get a drop-down list with all roles available.
If we choose Users and groups, we can assign the policy to an user or security group.
We can also make exclusions to the assignment configured on the Include tab, this can be done on the Exclude tab.
Here we have the same options as on the Include tab.
- Choose your assignment on the Include tab
- Choose your exclusion
- Click Done
- Browse to Cloud apps
On the Cloud apps or actions tab we determine to which cloud app the policy is applied.
We can assign the policy to All cloud apps or just one. When searching on SharePoint, SharePoint is shown, but also the new Office 365 option which is in preview. Office 365 contains multiple cloud apps.
- Click Select app
- Search for SharePoint
- Select SharePoint
- Click Done
- Browse to Conditions
If we choose SharePoint, this policy also affects Teams, Planner,Delve, MyAnalytics and Newsfeed. Something to keep in mind.
One other option found under Cloud apps or actions, is the option to Register Security information. More on that in this previous post.
We don`t use this option in this setup.
Under Conditions we find Sign-in risk, Device platforms, Locations, Clients apps and device state.
With sign-in risk we can trigger for example a MFA challenge, when the sign-in is marked as High risk.
Sign-in risk is part of Azure AD Identity Protection, and Azure AD Premium P2 feature, which is out of scope for this post.
On the Device platforms tab we determine on which device platform (Operating system) the policy is triggered.
We can choose to Include Any device, or only choose one platform.
I usually make two CA policies, separated on device platform.
Policy one includes Any device and as exclusion Android and iOS.
The second policy is set to include Android and iOS.
By setting one policy to Any device, you make sure unsupported platforms (like Linux) don`t bypass the CA policy and are blocked from accessing corporate data.
Policy one is in this case triggered on Windows and macOS.
- Set Configure to Yes
- Leave Any device selected
- On the Exclude tab
- Select Android and iOS
- Click Done
Under Locations we determine from which locations the policy is triggered.
This can be Any location, All trusted locations or a Selected location.
The section to create these location can also be found under Conditional Access.
We can set exclusions to the locations which triggers the policy, for example with MFA trusted IPs.
I leave the Locations section not configured, as I want the policy to apply, no matter what location.
On the Client apps tab we choose the client apps to which the policy is applied.
In case of SharePoint, the policy needs to be applied to Browsers and Mobile apps and desktop clients which support modern authentication.
We leave Other clients unchecked, as we create a separate policy to block these clients.
- Set Configure to Yes
- Select Browser
- Select Mobile apps and desktop clients
- Select Modern authentication clients
- Click Done
On the Device state tab we can exclude devices with a particular state from applying the policy.
We could use this option with our MFA policy, to exclude devices which are Hybrid AD joined or marked as Compliant.
As this option is in Preview and I can accomplish the same by using the Grant controls, I leave this not configured.
But if you want to use multiple (Grant) controls to be active, except on Hybrid AD Joined or Compliant devices, this is a great new option.
We move on to the Access controls section. Here we determine the requirements which needs to be satisfied before access is granted (or access blocked).
As I want the user to be challenged with MFA when accessing SharePoint, we need to check Require multi-factor authentication. But I don`t want the users to receive a MFA challenge when a Hybrid AD joined or Compliant device is used, therefore I also check these options. Just one of the controls is required to grant access.
- Select Grant access
- Select Require multi-factor authentication
- Select Require device to be marked as compliant
- Select Require Hybrid Azure AD joined device
- Select Require one of the selected controls
- Click Select
On the Sessions tab we have four session controls to enable limited experience within a cloud app.
With Use app enforced restrictions you can limit the experience for Exchange and SharePoint online on unmanaged devices as shown in this post.
Conditional Access App Control is used to connect the policy to Microsoft Cloud App Security.
With Sign-in frequency we control the time period before a user is asked to sign-in again when attempting to access a resource.
With Persistent browser session we control if users are allowed to remain signed in after closing and reopening their browser.
Although I want to restrict the experience for end-users when they access SharePoint from an unmanaged device, I leave everything in the sessions section not configured.
- Switch the policy to On
- Click Create
The Conditional Access policy for SharePoint Online is ready!
As I want to limit the experience for end-users when they use an unmanaged device, I show how that is done in the next part of this post.
In the last configuration part, I also show how to block apps which don`t use modern authentication (which use legacy authentication).
Limit SharePoint user experience from unmanaged devices
These restrictions are configured from the SharePoint Admin center, but the end-result is two Conditional Access policies are created to limited the user experience from unmanaged devices.
By setting these restrictions you still allow access to SharePoint Online from unmanaged (personal) devices, but you prevent downloading and syncing files to the local machine and prevent printing files.
- Open the SharePoint Admin center
- Browse to Policies – Access control
- Click Unmanaged devices
- Select Allow limited, web-only access
- Click Save
As you can read in de message in yellow, Apps that don`t use modern authentication are blocked.
This setting to block apps that don`t use modern authentication is also found under Access control.
The end result of setting these restrictions are two Conditional Access policies.
Block legacy authentication with a Conditional Access policy
The last policy we create is to block legacy authentication.
We target that policy to All users, Any device and All cloud apps.
We target Other clients on the Client apps tab.
- Give the policy a Name
- Select All users on the Users and groups tab
- Select All cloud apps on the Cloud apps and actions tab
- Browse to Conditions – Client apps
- Select Mobile apps and desktop clients
- Select Other clients
- Click Done (twice)
- Browse to Grant under Access controls
- Select Block access
- Click Select
- Switch the Policy to On
- Take note of the message
- Click Create
All policies are in place. When a users sign-ins from a personal device, the user receives a MFA challenge and is unable to download documents from SharePoint Online.
When the user sign-in to SharePoint Online from a Hybrid AD joined or device marked as compliant (Windows or macOS), the user isn`t challenged with MFA.
The user is unable to use a client which uses legacy authentication to access SharePoint Online (even if that app is used from a Hybrid joined or compliant device).
End-user experience
Let`s have a short look at the end-user experience on a Windows device.
As required, the user is challenged with multi-factor authentication when sign-in to SharePoint online from a unmanaged Windows 10 device.
And the user experience is limited when using a unmanged device. The user is restricted in downloading, printing and syncing documents. But the user is still able to view and edit document in the browser. This keeps the users productive with their personal devices.
On a device which is marked as compliant, the user doesn`t get a MFA challenge.
And the user is allowed to download, print and sync documents.
This was just an example of using Azure AD Conditional Access policies for SharePoint Online. A lot of combinations of conditions is possible to fine tune the policy to your own needs.
These CA policies can not be only used with all Office 365 apps, but these can be used for all your Enterprise apps which are connected to Azure Active Directory, including on-premises app made available via Azure Application Proxy. This makes CA policies very powerful in keeping your corporate data save.
You might also be interested in a comparable post about CA policies, but this one about Android and iOS. The article can be found here.
When you have any questions about this post, leave a comment or contact me via social media or email.

Why set;
Select Mobile apps and desktop clients
Select Other clients
In the block legacy CA policy and not just Other Clients?
😉
Other clients only becomes visible when you click Mobile apps and desktop cients, or Advanced. 🙂
Hi Peter,
Thanks for sharing this post! I have setup a similar policy to allow users to be productive from non-managed machines although I have found that on Intune managed devices which are compliant, based on which browser I use, I still get the limited experience across OWA and SPO.
ie, Windows 10 Intune managed & compliant
– IE = full access
– Chrome + Windows 10 Accounts extension = web view only
– New Edge Chromium Browser + Signed in = web view only
There’s nothing in the AAD Sign in logs which are obvious, what would you advise?
Thanks in advance!