This is the third blog post about managing local users and local rights on Windows 10 devices with Microsoft Intune. In this blog post I show how we can manage the local administrators group on a Hybrid Azure AD joined Windows 10 device.
I show how we can add a security group to the administrators group using the group name and SID. I also show how we can add a user account to the administrators group. This solution can also be used with other local groups, the Administrators group is just an example.
Like in the previous posts we need to use a Configuration Service Provider (CSP) policy and a Custom configuration profile to get the job done. This time we need to use the RestrictedGroups CSP.
All information for this CSP policy is found on Microsoft docs here.
Some notes to take into account; this policy overwrites the default members of the Administrators group. By default the local Administrator account and Domain Admins group are member of the local Administrators group. If you only want to add a group to the Administrators group and not want to remove the default groups, don`t forget to add the Administrator account and Domain Admins group to your policy.
Configure the Custom Configuration profile
- Sign-in to the Endpoint Manager admin center
- Browse to Devices – Windows
- On the Configurations profiles tab click + Create profile
- Choose Windows 10 and later as Platform
- Choose Custom as Profile type
- Click Create
- Give the configuration profile a Name
- Enter a Description (optional)
- Click the Settings tab
- Click Add
In the value field we set which group membership we like to manage and define the group members.
<accessgroup desc> contains the local group SID or group name.
<member name> contains the group members to add to the local group.
In this first example I add the Domain Admins group with the group name and a (local AD) group with the SID. I also add the local Administrators account to the group.
Name: RestrictedGroups – ConfigureGroupMembership
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/RestrictedGroups/ConfigureGroupMembership
Data Type: String
Value:
<groupmembership>
<accessgroup desc = "Administrators">
<member name = "Administrator" />
<member name = "peterklapwijk\Domain Admins" />
<member name = "S-1-5-21-997480969-2405514478-424995144-1131" />
</accessgroup>
</groupmembership>Click OK (twice) and click Create.
In the second example I add an user account from my (local AD) to the Administrators group.
Name: RestrictedGroups – ConfigureGroupMembership
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/RestrictedGroups/ConfigureGroupMembership
Data Type: String
Value:
<groupmembership>
<accessgroup desc = "Administrators">
<member name = "Administrator" />
<member name = "peterklapwijk\Domain Admins" />
<member name = "peterklapwijk\local.user01" />
</accessgroup>
</groupmembership>Assign the profile to a security group and your ready for testing.
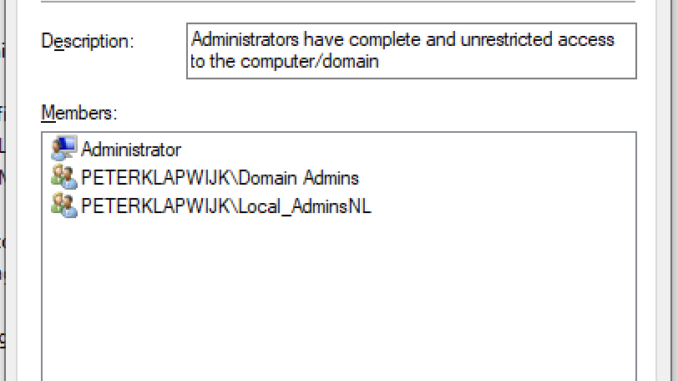
The end result
Before the policy is synced, the local Administrators account and Domain Admins group are member of the local Administrators group on a Windows 10 (Hybrid AD Joined) device.
In the first example I add an extra group to the local Administrators group using the SID of the AD group. As the AD is queried for the corresponding group name, the group name is shown, in this case Local_AdminNL.
In the second example I added an user account to the local Administrators group.
That`s is for this post. Thank you for reading.
If you are als interested in managing the local administrator group on Azure AD joined devices, read this article about adding AAD user accounts, or this post about adding an AAD group to the local administrators group.
Starting with Windows 10 build 20H2 we also have a new setting LocalUsersAndGroups.

This CSP Policy is OS language dependent.
It works fine with english operative system.
I´ve been 3 days working on it and it did only worked when I used the spanish name of administrators group and local administrator user
Administradores and Administrador.
404 event id
Never managed to get it working. Policy is crafted correctly, it shows as applied OK in Intune, there is no entry in local group ever
That is AD user *synced to AAD, so the whoami shows as domain\username)
I am searching for a way to change the local admin group description using Intune. I would like to put “Managed by Intune” in the local admin group description.
Thanks
instead of Administrators you can use the SID S-1-5-32-544 then it works on all language