I actually didn’t even notice it myself in the Azure AD portal but I was triggered by Scott Duffey his tweet, we have new dynamic device group properties available. And these are not just dynamic group properties, these are properties for which we are already screaming for years!
We finally have the option to use Mobile Device Management Type as property to create our dynamic device groups. We can now create a group with all our System Center Configuration Manager (SCCM) managed devices, or all our Intune managed devices.
But we now also have a property to set the Join Type, which means we can create groups for our Hybrid Azure AD Joined and Azure AD Joined devices.
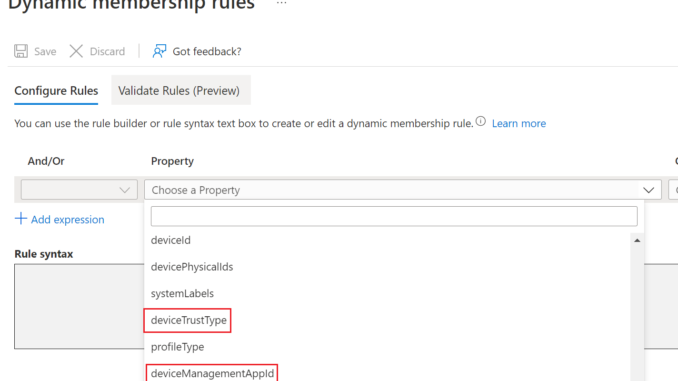
deviceTrustType is used to set the join type (ServerAd, AzureAd or Workplace).
deviceManagementAppId is used to set the MDM Management Type.
But as you can see we need to use an MDM App ID to configure this property, we can’t just use the name of the MDM solution as seen in the Azure portal. So let’s quickly look at how we can determine which ID we should use for Intune and SCCM.
Look up the MDM App Id
In the Azure AD portal, when we open the properties of our Windows devices it shows System Center Configuration Manager as MDM.
Or it shows Microsoft Intune as MDM.
It also shows the Object ID. With that object ID, we are able to look up the mdmAppId via Microsoft Graph Explorer, which we need to set the deviceManagementAppId in our dynamic device group.
To look up the Id, we do that by running this query:
https://graph.microsoft.com/v1.0/devices/[ObjectID]
Replace [ObjectID] with the object ID from your device.
When we run the query for an SCCM-managed device, we see the mdmAppId in the response:
54b943f8-d761-4f8d-951e-9cea1846db5a
And when we run the query for an Intune-managed device, the mdmAppId is:
0000000a-0000-0000-c000-000000000000
With this information, we can create a dynamic device group based on the MDM Type.
Create an AAD Dynamic group using the MDM Type
To create an AAD Dynamic device group using the MDM Type we need to select deviceManagementAppId as Property.
As a value, we enter one of the IDs we found via Graph Explorer:
54b943f8-d761-4f8d-951e-9cea1846db5a for SCCM.
0000000a-0000-0000-c000-000000000000 for Intune.
Depending on the operator you prefer, you need to enter the whole ID or can use a part of the ID.
If needed you can expand the dynamic query, for example with deviceOSType, or for a short while, also with deviceTrustType.
Thanks for reading!

Do either of these device management app IDs change with each domain or is it static and built into Azure from Microsoft?
is there a way to create a group based on device’s IPs