Last week I wrote this article to explain how Azure AD Conditional Access can be configured for Windows and macOS. In this post I show how a Conditional Access (CA) policy can be setup for Android and iOS.
Before we begin, what is a Conditional Access policy in short?
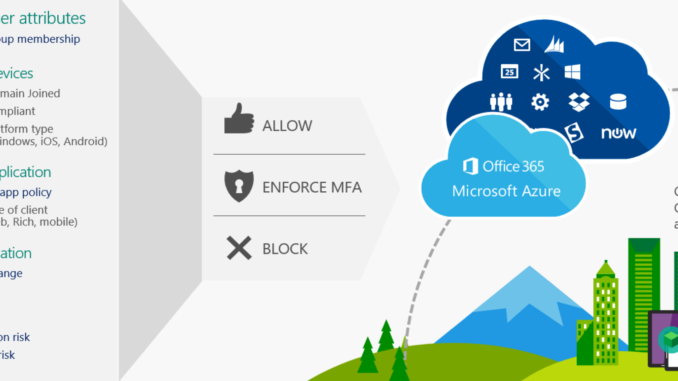
Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies. Actually it`s the principle of, if this, than that.
If your device is compliant, than you are granted access to Office 365. If your device is not compliant, access is blocked.
Some info in this post is exactly the same as in the previous post, this way it can be read as stand-alone post.
Azure AD Conditional Access is an Azure AD Premium feature.
Example setup
In this example I only want to allow access to Exchange Online when the Microsoft Outlook mobile app is used and the App Protection Policy is applied.
Configure a Conditional Access policy for Exchange Online
The Conditional Access section can be found in the Azure and Endpoint Manager (Intune) portal.
- Sign-in to the Azure portal
- Browse to Azure Active Directory – Security
- Choose Conditional Access
- Or sign-in to the Endpoint Manager admin center
- Browse to Endpoint Security
- Choose Conditional Access
On the Policies tab all existing Conditional Access policies are shown and here you create a new policy.
Click +New policy
The policy consists of two parts; Assignments and Access controls.
Under Assignments you set to which, what, where the policy set is applied.
Think of which group of users, what kind of devices (Operating system), which location and which cloud app.
Under Access controls you determine if access is blocked, or granted under certain controls. And here you find the session controls.
Let`s create a CA policy and see what options are available for configuration.
- Give the Policy a Name
- Click Users and groups
On the Include tab we determine to who the policy is applied. The policy can be assigned to All users, but you can also assign it to All guest and external users, Directory roles or Users and Groups (or a combination of these options).
If we choose Directory roles, we get a drop-down list with all roles available.
If we choose Users and groups, we can assign the policy to an user or security group.
We can also make exclusions to the assignment configured on the Include tab, this can be done on the Exclude tab.
Here we have the same options as on the Include tab.
- Choose your assignment on the Include tab
- Choose your exclusion
- Click Done
- Browse to Cloud apps
On the Cloud apps or actions tab we determine to which cloud app the policy is applied.
We can assign the policy to All cloud apps or just one. When searching on Exchange, Exchange Online is shown, but also the new Office 365 option which is in preview. Office 365 contains multiple cloud apps.
- Click Select app
- Search for Exchange Online
- Select Exchange Online
- Click Done
- Browse to Conditions
If we choose Exchange Online, this policy also affects apps such as OneDrive and Teams.
One other option found under Cloud apps or actions, is the option to Register Security information. More on that in this previous post.
We don`t use this option in this setup.
Under Conditions we find Sign-in risk, Device platforms, Locations, Clients apps and device state.
With sign-in risk we can trigger for example a MFA challenge, when the sign-in is marked as High risk.
Sign-in risk is part of Azure AD Identity Protection, and Azure AD Premium P2 feature, which is out of scope for this post.
On the Device platforms tab we determine on which device platform (Operating system) the policy is triggered.
We can choose to Include Any device, or only choose one platform.
I usually make two CA policies, separated on device platform.
Policy one includes Any device and as exclusion Android and iOS.
The second policy is set to include Android and iOS.
By setting one policy to Any device, you make sure unsupported platforms (like Linux) don`t bypass the CA policy and are blocked from accessing corporate data.
Policy one is in this case triggered on Windows and macOS.
- Set Configure to Yes
- Select Select device platforms
- Select Android
- Select iOS
- Click Done
Under Locations we determine from which locations the policy is triggered.
This can be Any location, All trusted locations or a Selected location.
The section to create these location can also be found under Conditional Access.
We can set exclusions to the locations which triggers the policy, for example with MFA trusted IPs.
I leave the Locations section not configured, as I want the policy to apply, no matter what location.
On the Client apps tab we choose the client apps to which the policy is applied.
In case of Exchange Online, the policy needs to be applied to Browsers and Mobile apps and desktop clients which support modern authentication.
We uncheck Other clients, as we create a separate policy to block these clients.
- Set Configure to Yes
- Uncheck Other clients
- Click Done
On the Device state tab we can exclude devices with a particular state from applying the policy.
In this case we leave it not configured.
We move on to the Access controls section. Here we determine the requirements which needs to be satisfied before access is granted (or access blocked).
In this case we only want to allow access to Exchange Online when Outlook (an approved app) is used and the App Protection Policy is applied.
- Select Grant access
- Select Require approved client app
- Select Require app protection policy
- Select Require all the selected controls
- Click Select
On the Sessions tab we have four session controls to enable limited experience within a cloud app.
With Use app enforced restrictions you can limit the experience for Exchange and SharePoint online on unmanaged devices as shown in this post.
Conditional Access App Control is used to connect the policy to Microsoft Cloud App Security.
With Sign-in frequency we control the time period before a user is asked to sign-in again when attempting to access a resource.
With Persistent browser session we control if users are allowed to remain signed in after closing and reopening their browser.
In this case we don`t use any of the session controls.
- Switch the policy to On
- Click Create
The Conditional Access policy for Exchange Online is ready.
I also want to block legacy authentication, like I also showed in the previous post, so we`ll be sure an (mail) app doesn`t bypass this policy.
If you`ve already created such policy, you can skip the next steps and move to the end-user experience.
Block legacy authentication with a Conditional Access policy
The second and last policy we create is to block legacy authentication.
We target that policy to All users, Any device and All cloud apps.
We target Other clients on the Client apps tab.
- Give the policy a Name
- Select All users on the Users and groups tab
- Select All cloud apps on the Cloud apps and actions tab
- Browse to Conditions – Client apps
- Select Mobile apps and desktop clients
- Select Other clients
- Click Done (twice)
- Browse to Grant under Access controls
- Select Block access
- Click Select
- Switch the Policy to On
- Take note of the message
- Click Create
Both policies are in-place.
With these policies we make sure Exchange Online is only accessible from an Android or iOS device, when an approved app is used (like Outlook) and the App Protection Policy is applied.
End-user experience
When an user tries to access the Exchange Online mailbox with an un-approved app, like Gmail, access is blocked.
The message describes that the app is not allowed to use and when the user clicks the URL, a list is shown with allowed (approved) apps.
When the user authenticates to the mailbox with the Outlook mobile app, a message is shown the devices needs to be registered.
This is done with a broker app, on Android this is the Company portal app.
When you click Get the app, the store is opened to download the app.
When the broker app is installed (no need to sign-in) and the user sign-ins to Outlook again, the device needs to be registered.
Click Register to start the registration proces.
When everything is ready, the mailbox is opened in Outlook and the App Protection policy is applied.
Depending on the different App Protection Policy settings which are applied, above screen shots might differ.
If you want to read more about App Protection policies, I suggest to read this article.
When you have any questions about this post, leave a comment or contact me via social media or email.

Hi Peter,
All the IOS devices are managed but 90% using the native mail app. So how do I force
for the Outlook app and reset the native mail profile?
How do I configure above customize messages screens?